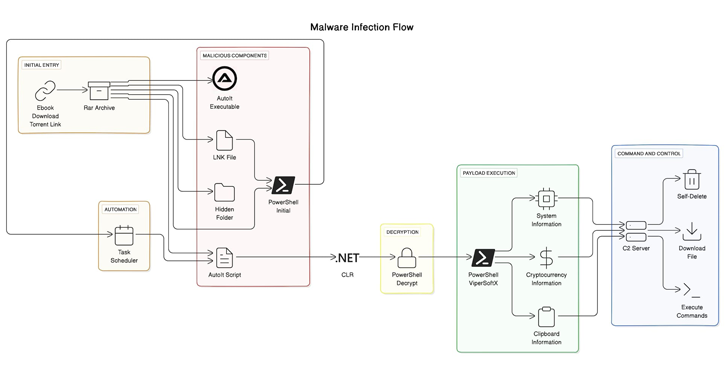
The subtle malware often called ViperSoftX has been noticed being distributed as eBooks over torrents.
“A notable facet of the present variant of ViperSoftX is that it makes use of the Frequent Language Runtime (CLR) to dynamically load and run PowerShell instructions, thereby making a PowerShell surroundings inside AutoIt for operations,” Trellix safety researchers Mathanraj Thangaraju and Sijo Jacob stated.
“By using CLR, ViperSoftX can seamlessly combine PowerShell performance, permitting it to execute malicious capabilities whereas evading detection mechanisms which may in any other case flag standalone PowerShell exercise.”
Initially detected by Fortinet in 2020, ViperSoftX is thought for its potential to exfiltrate delicate info from compromised Home windows hosts. Over time, the malware has grow to be a related instance of risk actors repeatedly innovating their ways in an try to remain stealthy and circumvent defenses.
That is exemplified by the elevated complexity and the adoption of superior anti-analysis methods equivalent to byte remapping and internet browser communication blocking, as documented by Pattern Micro in April 2023.
As not too long ago as Could 2024, malicious campaigns have leveraged ViperSoftX as a supply car to distribute Quasar RAT and one other info stealer named TesseractStealer.
Assault chains propagating the malware are identified to make use of cracked software program and torrent websites, however using eBook lures is a newly noticed method. Current inside the supposed eBook RAR archive file is a hidden folder in addition to a misleading Home windows shortcut file that purports to be a benign doc.
Executing the shortcut file initiates a multi-stage an infection sequence that begins with the extraction of PowerShell code that unhides the hid folder and units up persistence on the system to launch an AutoIt script that, in flip, interacts with the .NET CLR framework, to decrypt and run a secondary PowerShell script, which is ViperSoftX.
“AutoIt doesn’t by default assist the .NET Frequent Language Runtime (CLR),” the researchers stated. “Nevertheless, the language’s user-defined capabilities (UDF) supply a gateway to the CLR library, granting malevolent actors entry to PowerShell’s formidable capabilities.”
ViperSoftX harvests system info, scans for cryptocurrency wallets by way of browser extensions, captures clipboard contents, and dynamically downloads and runs further payloads and instructions primarily based on responses acquired from a distant server. It additionally comes with self-deletion mechanisms to problem detection.
“One of many hallmark options of ViperSoftX is its adept use of the Frequent Language Runtime (CLR) to orchestrate PowerShell operations inside the AutoIt surroundings,” the researchers stated. “This integration permits seamless execution of malicious capabilities whereas evading detection mechanisms that will sometimes flag standalone PowerShell exercise.”
“Moreover, ViperSoftX’s potential to patch the Antimalware Scan Interface (AMSI) earlier than executing PowerShell scripts underscores its dedication to bypass conventional safety measures.”