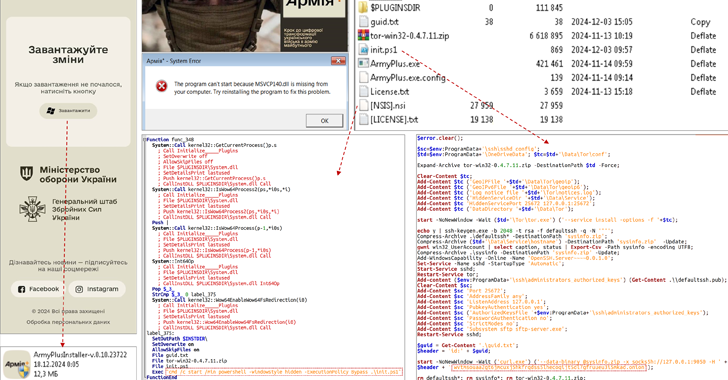
The Pc Emergency Response Crew of Ukraine (CERT-UA) has disclosed {that a} menace actor it tracks as UAC-0125 is leveraging Cloudflare Employees service to trick army personnel within the nation into downloading malware disguised as Military+, a cellular app that was launched by the Ministry of Defence again in August 2024 in an effort to make the armed forces go paperless.
Customers who go to the faux Cloudflare Employees web sites are prompted to obtain a Home windows executable of Military+, which is created utilizing Nullsoft Scriptable Set up System (NSIS), an open-source instrument used to create installers for the working system.
Opening the binary shows a decoy file to be launched, whereas additionally executing a PowerShell script that is designed to put in OpenSSH on the contaminated host, generate a pair of RSA cryptographic keys, add the general public key to the “authorized_keys” file, and transmit the personal key to an attacker-controlled server utilizing the TOR anonymity community.
The top aim of the assault is to permit the adversary to achieve distant entry to the sufferer’s machine, CERT-UA mentioned. It is at present not recognized how these hyperlinks are propagated.
The company additional famous that UAC-0125 is related to one other cluster referred to as UAC-0002, which is best referred to as APT44, FROZENBARENTS, Sandworm, Seashell Blizzard, and Voodoo Bear, a sophisticated persistent menace (APT) group with ties to Unit 74455 throughout the Principal Directorate of the Basic Employees of the Armed Forces of the Russian Federation (GRU).
Earlier this month, Fortra revealed it has noticed a “rising development in authentic service abuse,” with dangerous actors making use of Cloudflare Employees and Pages to host bogus Microsoft 365 login and human verification pages to steal customers’ credentials.
The corporate mentioned it has witnessed a 198% improve in phishing assaults on Cloudflare Pages, rising from 460 incidents in 2023 to 1,370 incidents as of mid-October 2024. Likewise, phishing assaults using Cloudflare Employees have surged by 104%, climbing from 2,447 incidents in 2023 to 4,999 incidents thus far.
The event comes because the European Council imposed sanctions towards 16 people and three entities that it mentioned had been chargeable for “Russia’s destabilizing actions overseas.”
This contains GRU Unit 29155, for its involvement in overseas assassinations, bombings, and cyber assaults throughout Europe, Groupe Panafricain pour le Commerce et l’Investissement, a disinformation community finishing up pro-Russian covert affect operations within the Central African Republic and Burkina Faso, and African Initiative, a information company that amplified Russian propaganda and disinformation in Africa.
The sanctions additionally goal Doppelganger, a Russia-led disinformation community recognized for disseminating narratives in assist of the Russia’s ongoing battle of aggression in Ukraine, manipulate public opinion towards the nation, and erode Western assist.
To that finish, Sofia Zakharova, the division head within the Workplace of the President of the Russian Federation for the Growth of Info and Communication Applied sciences and Communications Infrastructure, and Nikolai Tupikin, head and founding father of GK Struktura (aka Firm Group Structura), have been subjected to asset freezes and journey bans.
Tupikin was additionally sanctioned by the U.S. Treasury Division’s Workplace of International Property Management (OFAC) again in March 2024 for partaking in overseas malign affect campaigns.