A newly disclosed essential safety flaw impacting Progress Software program MOVEit Switch is already seeing exploitation makes an attempt within the wild shortly after particulars of the bug had been publicly disclosed.
The vulnerability, tracked as CVE-2024-5806 (CVSS rating: 9.1), issues an authentication bypass that impacts the next variations –
- From 2023.0.0 earlier than 2023.0.11
- From 2023.1.0 earlier than 2023.1.6, and
- From 2024.0.0 earlier than 2024.0.2
“Improper authentication vulnerability in Progress MOVEit Switch (SFTP module) can result in Authentication Bypass,” the corporate stated in an advisory launched Tuesday.
Progress has additionally addressed one other essential SFTP-associated authentication bypass vulnerability (CVE-2024-5805, CVSS rating: 9.1) affecting MOVEit Gateway model 2024.0.0.
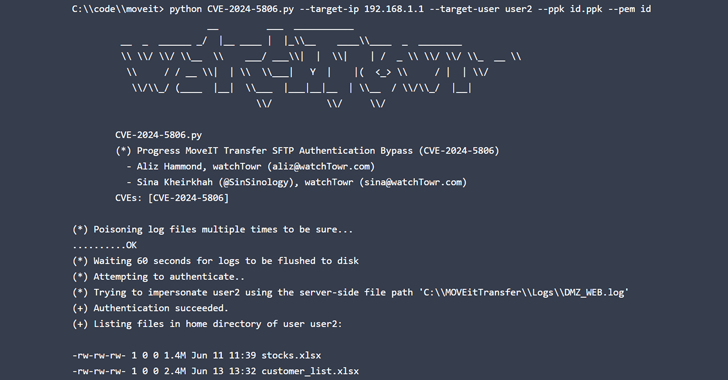
Profitable exploitation of the failings might permit attackers to bypass SFTP authentication and achieve entry to MOVEit Switch and Gateway techniques.
watchTowr Labs has since revealed extra technical specifics about CVE-2024-5806, with safety researchers Aliz Hammond and Sina Kheirkhah noting that it may very well be weaponized to impersonate any consumer on the server.
The cybersecurity firm additional described the flaw as comprising two separate vulnerabilities, one in Progress MOVEit and the opposite within the IPWorks SSH library.
“Whereas the extra devastating vulnerability, the flexibility to impersonate arbitrary customers, is exclusive to MOVEit, the much less impactful (however nonetheless very actual) pressured authentication vulnerability is prone to have an effect on all functions that use the IPWorks SSH server,” the researchers stated.
Progress Software program stated the shortcoming within the third-party element “elevates the danger of the unique subject” if left unpatched, urging clients to observe the beneath two steps –
- Block public inbound RDP entry to MOVEit Switch server(s)
- Restrict outbound entry to solely identified trusted endpoints from MOVEit Switch server(s)
In keeping with Rapid7, there are three conditions to leveraging CVE-2024-5806: Attackers must have data of an present username, the goal account can authenticate remotely, and the SFTP service is publicly accessible over the web.
As of June 25, information gathered by Censys exhibits that there are round 2,700 MOVEit Switch situations on-line, most of them situated within the U.S., the U.Okay., Germany, the Netherlands, Canada, Switzerland, Australia, France, Eire, and Denmark.
With one other essential subject in MOVEit Switch broadly abused in a spate of Cl0p ransomware assaults final 12 months (CVE-2023-34362, CVSS rating: 9.8), it is important that customers transfer shortly to replace to the most recent variations.
The event comes because the U.S. Cybersecurity and Infrastructure Safety Company (CISA) revealed that its Chemical Safety Evaluation Software (CSAT) was focused earlier this January by an unknown menace actor by profiting from safety flaws within the Ivanti Join Safe (ICS) equipment (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893).
“This intrusion might have resulted within the potential unauthorized entry of High-Display surveys, Safety Vulnerability Assessments, Web site Safety Plans, Personnel Surety Program (PSP) submissions, and CSAT consumer accounts,” the company stated, including it discovered no proof of knowledge exfiltration.