Cybersecurity researchers have uncovered a brand new Android distant entry trojan (RAT) referred to as BingoMod that not solely performs fraudulent cash transfers from the compromised units but in addition wipes them in an try and erase traces of the malware.
Italian cybersecurity agency Cleafy, which found the RAT in the direction of the top of Might 2024, mentioned the malware is underneath energetic improvement. It attributed the Android trojan to a possible Romanian-speaking risk actor owing to the presence of Romanian language feedback within the supply code related to early variations.
“BingoMod belongs to the fashionable RAT technology of cell malware, as its distant entry capabilities permit risk actors (TAs) to conduct Account Takeover (ATO) immediately from the contaminated system, thus exploiting the on-device fraud (ODF) approach,” researchers Alessandro Strino and Simone Mattia mentioned.
It is price mentioning right here that this method has been noticed in different Android banking trojans, similar to Medusa (aka TangleBot), Copybara, and TeaBot (aka Anatsa).
BingoMod, like BRATA, additionally stands out for using a self-destruction mechanism that is designed to take away any proof of the fraudulent switch on the contaminated system in order to hinder forensic evaluation. Whereas this performance is proscribed to the system’s exterior storage, it is suspected that the distant entry options may very well be used to provoke a whole manufacturing facility reset.

A number of the recognized apps masquerade as antivirus instruments and an replace for Google Chrome. As soon as put in through smishing ways, the app prompts the person to grant it accessibility companies permissions, utilizing it to provoke malicious actions.
This consists of executing the principle payload and locking out the person from the principle display screen to gather system data, which is then exfiltrated to an attacker-controlled server. It additionally abuses the accessibility companies API to steal delicate data displayed on the display screen (e.g., credentials and checking account balances) and provides itself permission to intercept SMS messages.

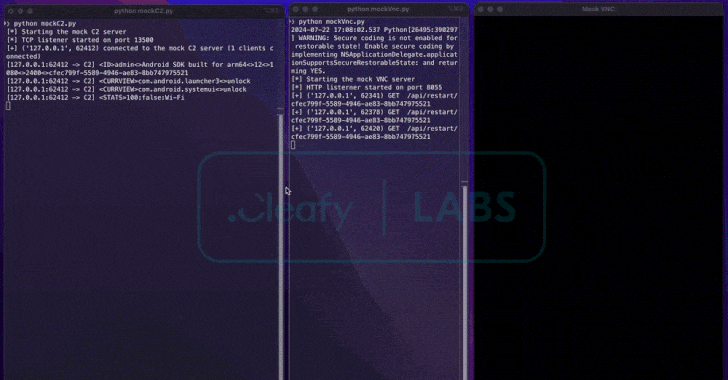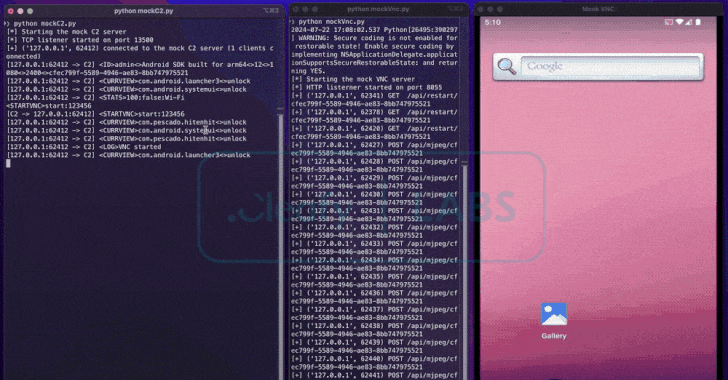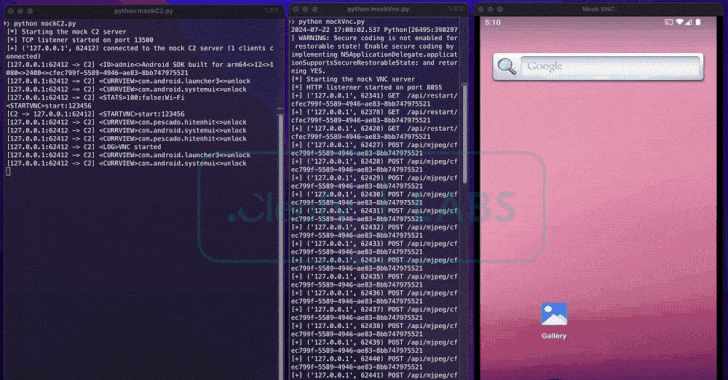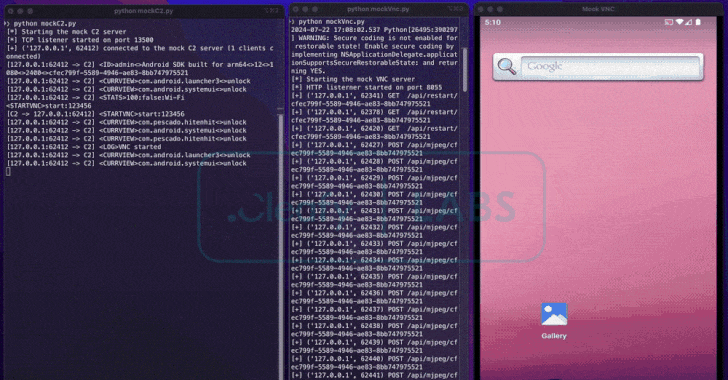
To provoke cash transfers immediately from compromised units, BingoMod establishes a socket-based reference to the command-and-control infrastructure (C2) to obtain as many as 40 instructions remotely to take screenshots utilizing Android’s Media Projection API and work together with the system in real-time.
This additionally implies that the ODF approach depends on a dwell operator to carry out a cash switch of as much as €15,000 (~$16,100) per transaction versus leveraging an Automated Switch System (ATS) to hold out monetary fraud at scale.
One other essential side is the risk actor’s emphasis on evading detection utilizing code obfuscation methods and the flexibility to uninstall arbitrary apps from the compromised system, indicating that the malware authors are prioritizing simplicity over superior options.
“Along with real-time display screen management, the malware reveals phishing capabilities by Overlay Assaults and pretend notifications,” the researchers mentioned. “Unusually, overlay assaults aren’t triggered when particular goal apps are opened however are initiated immediately by the malware operator.”