Microsoft has disclosed a high-severity Trade Server vulnerability that permits attackers to forge professional senders on incoming emails and make malicious messages much more efficient.
The safety flaw (CVE-2024-49040) impacts Trade Server 2016 and 2019, and was found by Solidlab safety researcher Vsevolod Kokorin, who reported it to Microsoft earlier this 12 months.
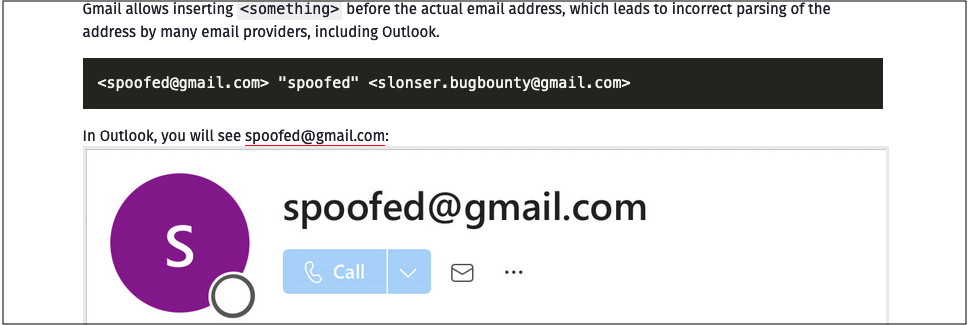
“The issue is that SMTP servers parse the recipient deal with otherwise, which ends up in e-mail spoofing,” Kokorin mentioned in a Might report.
“One other concern I found is that some e-mail suppliers enable the usage of the symbols < and > in group names, which doesn’t adjust to RFC requirements.”
“Throughout my analysis, I didn’t discover a single mail supplier that accurately parses the ‘From’ area in response to RFC requirements,” he added.
Microsoft additionally warned in the present day that the flaw could possibly be utilized in spoofing assaults concentrating on Trade servers and launched a number of updates throughout this month’s Patch Tuesday so as to add exploitation detection and warnings banners.
“The vulnerability is attributable to the present implementation of the P2 FROM header verification, which occurs in transport,” Microsoft defined.
“The present implementation permits some non-RFC 5322 compliant P2 FROM headers to go which may result in the e-mail consumer (for instance, Microsoft Outlook) displaying a solid sender as if it had been professional.”
Trade servers now warn of exploitation
Whereas Microsoft has not patched the vulnerability and can settle for emails with these malformed headers, the corporate says Trade servers will now detect and prepend a warning to malicious emails after putting in the Trade Server November 2024 Safety Replace (SU).
CVE-2024-49040 exploitation detection and e-mail warnings will probably be enabled by default on all techniques the place admins allow safe by default settings.
Up-to-date Trade servers will even add a warning to the physique of any emails it detects as having a solid sender and an X-MS-Trade-P2FromRegexMatch header to permit admins to reject phishing emails trying to use this flaw utilizing customized mail circulation guidelines.
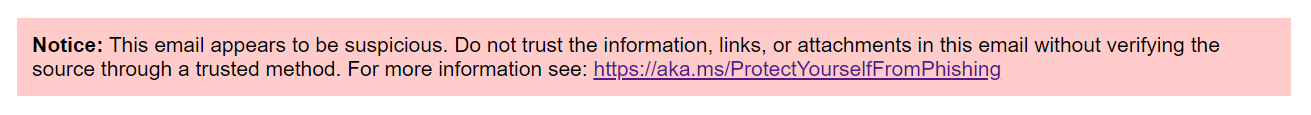
“Discover: This e-mail seems to be suspicious. Don’t belief the knowledge, hyperlinks, or attachments on this e-mail with out verifying the supply by means of a trusted technique,” the warning reads.
Whereas not suggested, the corporate supplies the next PowerShell command for individuals who nonetheless need to disable this new safety characteristic (run it from an elevated Trade Administration Shell):
New-SettingOverride -Title "DisableNonCompliantP2FromProtection" -Element "Transport" -Part "NonCompliantSenderSettings" -Parameters @("AddDisclaimerforRegexMatch=false") -Purpose "Disabled For Troubleshooting"
Get-ExchangeDiagnosticInfo -Course of Microsoft.Trade.Listing.TopologyService -Element VariantConfiguration -Argument Refresh
“Though it is potential to disable the characteristic utilizing New-SettingOverride, we strongly suggest you allow the characteristic enabled, as disabling the characteristic makes it simpler for unhealthy actors to run phishing assaults in opposition to your group,” Redmond warned.









