Installers for 3 totally different software program merchandise developed by an Indian firm named Conceptworld have been trojanized to distribute information-stealing malware.
The installers correspond to Notezilla, RecentX, and Copywhiz, in line with cybersecurity agency Rapid7, which found the availability chain compromise on June 18, 2024. The problem has since been remediated by Conceptworld as of June 24 inside 12 hours of accountable disclosure.
“The installers had been trojanized to execute information-stealing malware that has the aptitude to obtain and execute further payloads,” the corporate stated, including the malicious variations had a bigger file dimension than their authentic counterparts.
Particularly, the malware is provided to steal browser credentials and cryptocurrency pockets info, log clipboard contents and keystrokes, and obtain and execute further payloads on contaminated Home windows hosts. It additionally units up persistence utilizing a scheduled activity to execute the principle payload each three hours.
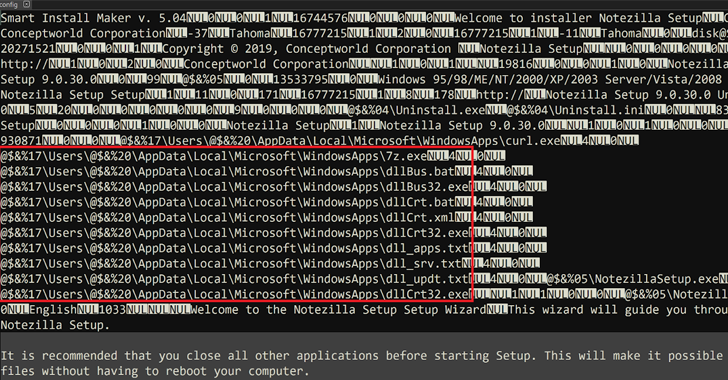
It is at present not clear how the official area “conceptworld[.]com” was breached to stage the counterfeit installers. Nevertheless, as soon as launched, the person is prompted to proceed with the set up course of related to the precise software program, whereas it is also designed to drop and execute a binary “dllCrt32.exe” that is liable for working a batch script “dllCrt.bat.”
Apart from establishing persistence on the machine, it is configured to execute one other file (“dllBus32.exe”), which, in flip, establishes connections with a command-and-control (C2) server and incorporates performance to steal delicate knowledge in addition to retrieve and run extra payloads.
This consists of gathering credentials and different info from Google Chrome, Mozilla Firefox, and a number of cryptocurrency wallets (e.g., Atomic, Coinomi, Electrum, Exodus, and Guarda). It is also able to harvesting recordsdata matching a particular set of extensions (.txt, .doc, .png, and .jpg), logging keystrokes, and grabbing clipboard contents.
“The malicious installers noticed on this case are unsigned and have a file dimension that’s inconsistent with copies of the authentic installer,” Rapid7 stated.
Customers who’ve downloaded an installer for Notezilla, RecentX, or Copywhiz in June 2024 are advisable to look at their techniques for indicators of compromise and take acceptable motion – corresponding to re-imaging the affected ones – to undo the nefarious modifications.