The malware often called GootLoader continues to be in lively use by risk actors trying to ship extra payloads to compromised hosts.
“Updates to the GootLoader payload have resulted in a number of variations of GootLoader, with GootLoader 3 at present in lively use,” cybersecurity agency Cybereason stated in an evaluation printed final week.
“Whereas among the particulars of GootLoader payloads have modified over time, an infection methods and total performance stay just like the malware’s resurgence in 2020.”
GootLoader, a malware loader a part of the Gootkit banking trojan, is linked to a risk actor named Hive0127 (aka UNC2565). It abuses JavaScript to obtain post-exploitation instruments and is distributed through search engine marketing (website positioning) poisoning techniques.
It usually serves as a conduit for delivering varied payloads comparable to Cobalt Strike, Gootkit, IcedID, Kronos, REvil, and SystemBC.

In latest months, the risk actors behind GootLoader have additionally unleashed their very own command-and-control (C2) and lateral motion instrument dubbed GootBot, indicating that the “group is increasing their market to achieve a wider viewers for his or her monetary features.”
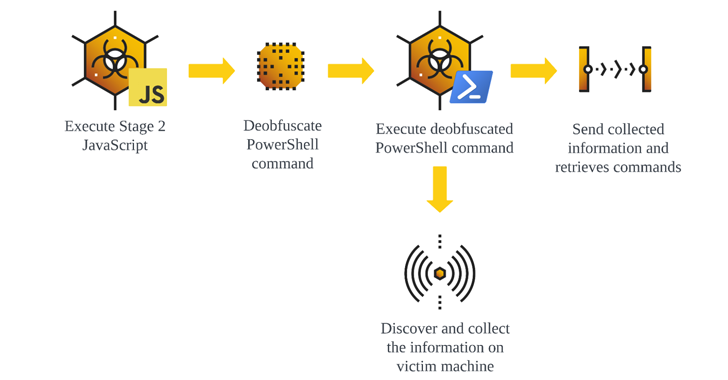
Assault chains contain compromising web sites to host the GootLoader JavaScript payload by passing it off as authorized paperwork and agreements, which, when launched, units up persistence utilizing a scheduled process and executes extra JavaScript to kick-start a PowerShell script for accumulating system info and awaiting additional directions.
“Websites that host these archive information leverage Search Engine Optimization (website positioning) poisoning methods to lure in victims which are trying to find business-related information comparable to contract templates or authorized paperwork,” safety researchers Ralph Villanueva, Kotaro Ogino, and Gal Romano stated.
The assaults are additionally notable for making use of supply code encoding, management stream obfuscation, and payload dimension inflation so as to withstand evaluation and detection. One other approach entails embedding the malware in reputable JavaScript library information like jQuery, Lodash, Maplace.js, and tui-chart.
“GootLoader has obtained a number of updates throughout its life cycle, together with adjustments to evasion and execution functionalities,” the researchers concluded.