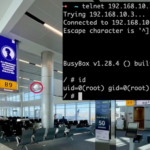
Cybersecurity firm Acronis is warning {that a} now-patched important safety flaw impacting its Cyber Infrastructure (ACI) product has been exploited within the wild.
The vulnerability, tracked as CVE-2023-45249 (CVSS rating: 9.8), issues a case of distant code execution that stems from using default passwords.
The flaw impacts the next variations of Acronis Cyber Infrastructure (ACI) –
- < construct 5.0.1-61
- < construct 5.1.1-71
- < construct 5.2.1-69
- < construct 5.3.1-53, and
- < construct 5.4.4-132
It has been addressed in variations 5.4 replace 4.2, 5.2 replace 1.3, 5.3 replace 1.3, 5.0 replace 1.4, and 5.1 replace 1.2 launched in late October 2023.
There are at the moment no particulars on how the vulnerability is being weaponized in real-world cyber assaults and the id of the menace actors that could be exploiting it.
Nonetheless, the Swiss-headquartered firm acknowledged stories of lively exploitation in an up to date advisory final week. “This vulnerability is understood to be exploited within the wild,” it stated.
Customers of affected variations of ACI are beneficial to replace to the newest model to mitigate potential threats.