A China-linked menace actor referred to as APT17 has been noticed focusing on Italian firms and authorities entities utilizing a variant of a recognized malware known as 9002 RAT.
The 2 focused assaults came about on June 24 and July 2, 2024, Italian cybersecurity firm TG Comfortable mentioned in an evaluation printed final week.
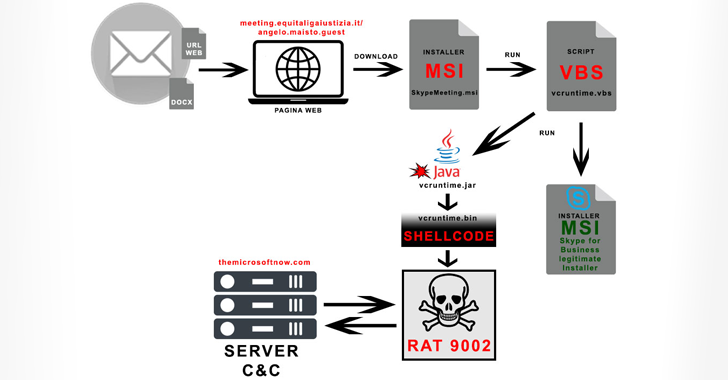
“The primary marketing campaign on June 24, 2024 used an Workplace doc, whereas the second marketing campaign contained a hyperlink,” the corporate famous. “Each campaigns invited the sufferer to put in a Skype for Enterprise bundle from a hyperlink of an Italian government-like area to convey a variant of 9002 RAT.”
APT17 was first documented by Google-owned Mandiant (then FireEye) in 2013 as a part of cyber espionage operations referred to as DeputyDog and Ephemeral Hydra that leveraged zero-day flaws in Microsoft’s Web Explorer to breach targets of curiosity.
It is also recognized by the monikers Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers, with the adversary sharing some stage of tooling overlap with one other menace actor dubbed Webworm.
9002 RAT, aka Hydraq and McRAT, achieved notoriety because the cyber weapon of selection in Operation Aurora that singled out Google and different massive firms in 2009. It was additionally subsequently put to make use of in one other 2013 marketing campaign named Sunshop wherein the attackers injected malicious redirects into a number of web sites.
The newest assault chains entail using spear-phishing lures to trick recipients into clicking on a hyperlink that urges them to obtain an MSI installer for Skype for Enterprise (“SkypeMeeting.msi”).
Launching the MSI bundle triggers the execution of a Java archive (JAR) file by way of a Visible Fundamental Script (VBS), whereas additionally putting in the respectable chat software program on the Home windows system. The Java utility, in flip, decrypts and executes the shellcode accountable for launching 9002 RAT.
A modular trojan, 9002 RAT comes with options to observe community site visitors, seize screenshots, enumerate information, handle processes, and run further instructions obtained from a distant server to facilitate community discovery, amongst others.
“The malware seems to be always up to date with diskless variants as nicely,” TG Comfortable mentioned. “It’s composed of assorted modules which are activated as wanted by the cyber actor in order to scale back the potential of interception.”