AI in Art: Everything You Should Know About Its Role and Future
There's a well-known quote by Albert Einstein that claims, “Creativity is intelligence…
10 Min Read
Secret Blizzard Deploys Kazuar Backdoor in Ukraine Using Amadey Malware-as-a-Service
The Russian nation-state actor tracked as Secret Blizzard has been noticed leveraging…
5 Min Read
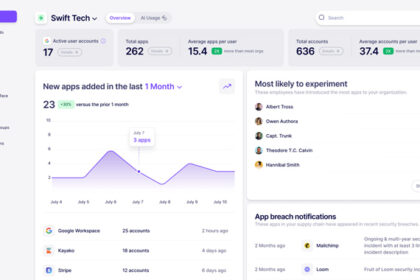
What is Nudge Security and How Does it Work?
In as we speak's extremely distributed office, each worker has the flexibility…
8 Min Read
U.S. Charges Chinese Hacker for Exploiting Zero-Day in 81,000 Sophos Firewalls
The U.S. authorities on Tuesday unsealed prices in opposition to a Chinese…
6 Min Read
LambdaTest Raises $38M to Advance Software Quality Assurance with KaneAI, the Intelligent Testing Assistant
As software program groups race to ship seamless, high-quality digital experiences, LambdaTest—a…
6 Min Read
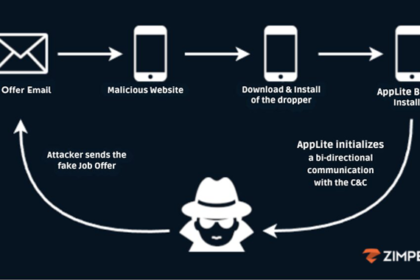
Fake Recruiters Distribute Banking Trojan via Malicious Apps in Phishing Scam
Cybersecurity researchers have make clear a classy cell phishing (aka mishing) marketing…
5 Min Read
Claude’s Model Context Protocol (MCP): A Developer’s Guide
Anthropic's Mannequin Context Protocol (MCP) is an open-source protocol that permits safe,…
7 Min Read
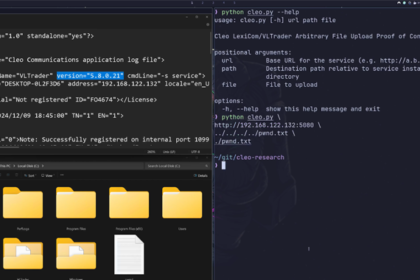
Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
Customers of Cleo-managed file switch software program are being urged to make…
5 Min Read