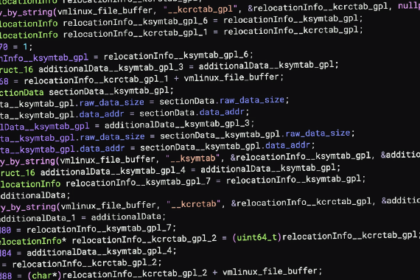
New Linux Rootkit PUMAKIT Uses Advanced Stealth Techniques to Evade Detection
Cybersecurity researchers have uncovered a brand new Linux rootkit referred to as…
3 Min Read
How to Generate a CrowdStrike RFM Report With AI in Tines
Run by the crew at orchestration, AI, and automation platform Tines, the…
8 Min Read
Why Analog AI Could Be the Future of Energy-Efficient Computing
Synthetic intelligence has remodeled the way in which we stay, powering instruments…
9 Min Read
Thai Officials Targeted in Yokai Backdoor Campaign Using DLL Side-Loading Techniques
Thai authorities officers have emerged because the goal of a brand new…
5 Min Read
Germany Disrupts BADBOX Malware on 30,000 Devices Using Sinkhole Action
Germany's Federal Workplace of Data Safety (BSI) has introduced that it has…
3 Min Read
DoJ Indicts 14 North Koreans for $88M IT Worker Fraud Scheme Over Six Years
The U.S. Division of Justice (DoJ) has indicted 14 nationals belonging to…
8 Min Read
Gemini 2.0: Meet Google’s New AI Agents
Whereas present AI assistants excel at responding to queries, the launch of…
8 Min Read
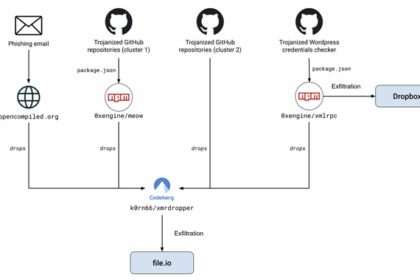
390,000+ WordPress Credentials Stolen via Malicious GitHub Repository Hosting PoC Exploits
A now-removed GitHub repository that marketed a WordPress software to publish posts…
5 Min Read