Meta’s COCONUT: The AI Method That Thinks Without Language
Understanding COCONUT's InnovationImage the distinction between talking your ideas out loud and…
5 Min Read
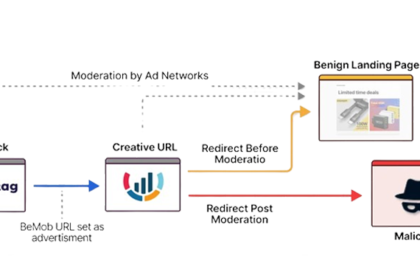
DeceptionAds Delivers 1M+ Daily Impressions via 3,000 Sites, Fake CAPTCHA Pages
Cybersecurity researchers have make clear a beforehand undocumented side related to ClickFix-style…
4 Min Read
NoviSpy Spyware Installed on Journalist’s Phone After Unlocking It With Cellebrite Tool
A Serbian journalist had his cellphone first unlocked by a Cellebrite device…
6 Min Read
Ukrainian Minors Recruited for Cyber Ops and Reconnaissance in Russian Airstrikes
The Safety Service of Ukraine (SBU or SSU) has uncovered a novel…
3 Min Read
Microsoft MFA AuthQuake Flaw Enabled Unlimited Brute-Force Attempts Without Alerts
Cybersecurity researchers have flagged a "essential" safety vulnerability in Microsoft's multi-factor authentication…
4 Min Read
WordPress Hunk Companion Plugin Flaw Exploited to Silently Install Vulnerable Plugins
Malicious actors are exploiting a vital vulnerability within the Hunk Companion plugin…
3 Min Read
SaaS Budget Planning Guide for IT Professionals
SaaS companies are one of many greatest drivers of OpEx (working bills)…
19 Min Read
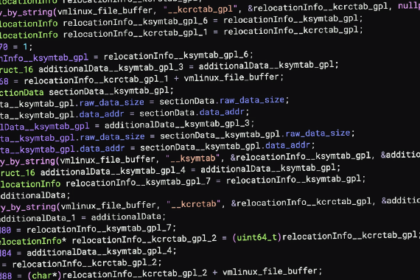
New Linux Rootkit PUMAKIT Uses Advanced Stealth Techniques to Evade Detection
Cybersecurity researchers have uncovered a brand new Linux rootkit referred to as…
3 Min Read