A number of organizations working inside world delivery and logistics, media and leisure, know-how, and automotive sectors in Italy, Spain, Taiwan, Thailand, Turkey, and the U.Okay. have develop into the goal of a “sustained marketing campaign” by the prolific China-based APT41 hacking group.
“APT41 efficiently infiltrated and maintained extended, unauthorized entry to quite a few victims’ networks since 2023, enabling them to extract delicate knowledge over an prolonged interval,” Google-owned Mandiant mentioned in a brand new report printed Thursday.
The menace intelligence agency described the adversarial collective as distinctive amongst China-nexus actors owing to its use of “private malware usually reserved for espionage operations in actions that seem to fall exterior the scope of state-sponsored missions.”
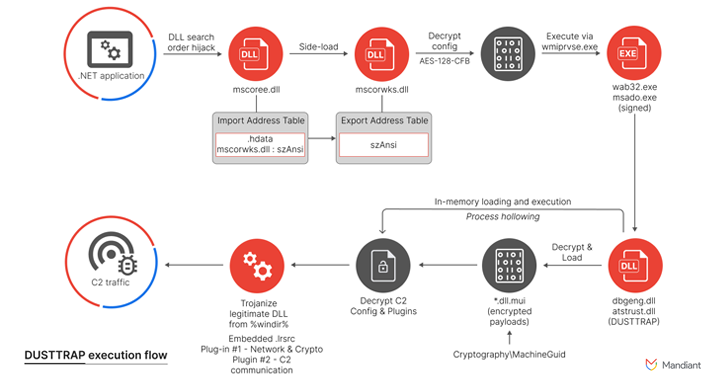
Assault chains contain using net shells (ANTSWORD and BLUEBEAM), customized droppers (DUSTPAN and DUSTTRAP), and publicly out there instruments (SQLULDR2 and PINEGROVE) to attain persistence, ship extra payloads, and exfiltrate knowledge of curiosity.
The online shells act as a conduit to obtain the DUSTPAN (aka StealthVector) dropper that is accountable for loading Cobalt Strike Beacon for command-and-control (C2) communication, adopted by the deployment of the DUSTTRAP dropper submit lateral motion.
DUSTTRAP, for its half, is configured to decrypt a malicious payload and execute it in reminiscence, which, in flip, establishes contact with an attacker-controlled server or a compromised Google Workspace account in an try to hide its malicious actions.
Google mentioned the recognized Workspace accounts have been remediated to stop unauthorized entry. It, nonetheless, didn’t reveal what number of accounts have been affected.
The intrusions are additionally characterised by way of SQLULDR2 to export knowledge from Oracle Databases to an area text-based file and PINEGROVE to transmit massive volumes of delicate knowledge from compromised networks by abusing Microsoft OneDrive as an exfiltration vector.
It is value noting right here that the malware households that Mandiant tracks as DUSTPAN and DUSTTRAP share overlaps with these which were codenamed DodgeBox and MoonWalk, respectively, by Zscaler ThreatLabz.

“DUSTTRAP is a multi-stage plugin framework with a number of parts,” Mandiant researchers mentioned, including it recognized no less than 15 plugins which might be able to executing shell instructions, finishing up file system operations, enumerating and terminating processes, capturing keystrokes and screenshots, gathering system info, and modifying Home windows Registry.
It is also engineered to probe distant hosts, carry out area identify system (DNS) lookups, listing distant desktop periods, add recordsdata, and conduct numerous manipulations to Microsoft Energetic Listing.
“The DUSTTRAP malware and its related parts that have been noticed throughout the intrusion have been code signed with presumably stolen code signing certificates,” the corporate mentioned. “One of many code signing certificates appeared to be associated to a South Korean firm working within the gaming trade sector.”
GhostEmperor Comes Again to Hang-out
The disclosure comes as Israeli cybersecurity firm Sygnia revealed particulars of a cyber assault marketing campaign mounted by a complicated China-nexus menace group known as GhostEmperor to ship a variant of the Demodex rootkit.
The precise technique used to breach targets is at the moment not clear, though the group has been beforehand noticed exploiting identified flaws in internet-facing functions. The preliminary entry facilitates the execution of a Home windows batch script, which drops a Cupboard archive (CAB) file to finally launch a core implant module.
The implant is supplied to handle C2 communications and set up the Demodex kernel rootkit through the use of an open-source undertaking named Cheat Engine to get across the Home windows Driver Signature Enforcement (DSE) mechanism.
“GhostEmperor employs a multi-stage malware to attain stealth execution and persistence and makes use of a number of strategies to impede evaluation course of,” Safety researcher Dor Nizar mentioned.