A risk actor that was beforehand noticed utilizing an open-source community mapping software has significantly expanded their operations to contaminate over 1,500 victims.
Sysdig, which is monitoring the cluster beneath the identify CRYSTALRAY, stated the actions have witnessed a tenfold surge, including it contains “mass scanning, exploiting a number of vulnerabilities, and putting backdoors utilizing a number of [open-source software] safety instruments.”
The first goal of the assaults is to reap and promote credentials, deploy cryptocurrency miners, and keep persistence in sufferer environments. A majority of the infections are concentrated within the U.S., China, Singapore, Russia, France, Japan, and India, amongst others.
Outstanding among the many open-source applications utilized by the risk actor is SSH-Snake, which was first launched in January 2024. It has been described as a software to hold out computerized community traversal utilizing SSH non-public keys found on methods.
The abuse of the software program by CRYSTALRAY was documented by the cybersecurity firm earlier this February, with the software deployed for lateral motion following the exploitation of identified safety flaws in public-facing Apache ActiveMQ and Atlassian Confluence cases.
Joshua Rogers, the developer behind SSH-Snake, instructed The Hacker Information on the time that the software solely automates what would have been in any other case handbook steps, and known as on corporations to “uncover the assault paths that exist – and repair them.”

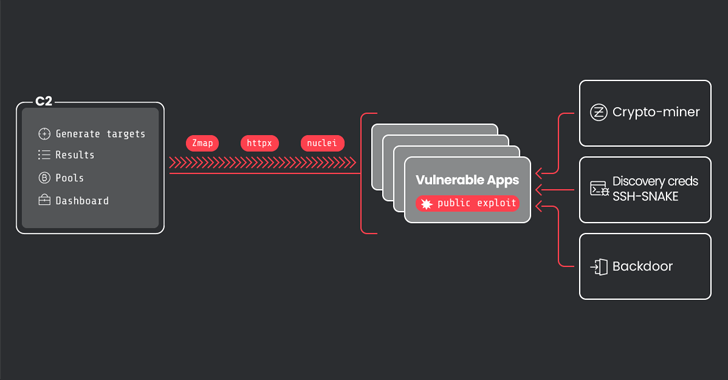
Among the different instruments employed by the attackers embrace asn, zmap, httpx, and nuclei in an effort to verify if a site is lively and launch scans for weak companies akin to Apache ActiveMQ, Apache RocketMQ, Atlassian Confluence, Laravel, Metabase, Openfire, Oracle WebLogic Server, and Solr.
CRYSTALRAY additionally weaponizes its preliminary foothold to conduct a wide-ranging credential discovery course of that goes past transferring between servers accessible through SSH. Persistent entry to the compromised atmosphere is achieved via a professional command-and-control (C2) framework known as Sliver and a reverse shell supervisor codenamed Platypus.
In an additional bid to derive financial worth from the contaminated property, cryptocurrency miner payloads are delivered to illicitly use the sufferer assets for monetary acquire, whereas concurrently taking steps to terminate competing miners that will have already been working on the machines.
“CRYSTALRAY is ready to uncover and extract credentials from weak methods, that are then bought on black markets for hundreds of {dollars},” Sysdig researcher Miguel Hernández stated. “The credentials being bought contain a mess of companies, together with Cloud Service Suppliers and SaaS e mail suppliers.”