Cybersecurity researchers have make clear a beforehand undocumented side related to ClickFix-style assaults that hinge on making the most of a single advert community service as a part of a malvertising-driven info stealer marketing campaign dubbed DeceptionAds.
“Completely reliant on a single advert community for propagation, this marketing campaign showcases the core mechanisms of malvertising — delivering over 1 million day by day ‘advert impressions’ [in the last ten days] and inflicting 1000’s of day by day victims to lose their accounts and cash by way of a community of three,000+ content material websites funneling site visitors,” Nati Tal, head of Guardio Labs, mentioned in a report shared with The Hacker Information.
The campaigns, as documented by a number of cybersecurity corporations in current months, contain directing guests of pirated film websites and others to bogus CAPTCHA verification pages that instruct them to repeat and execute a Base64-encoded PowerShell command, finally resulting in the deployment of knowledge stealers like Lumma.
The assaults are now not confined to a single actor, with Proofpoint just lately stating that a number of “unattributed” risk clusters have embraced the intelligent social engineering method to ship distant entry trojans, stealers, and even post-exploitation frameworks akin to Brute Ratel C4.

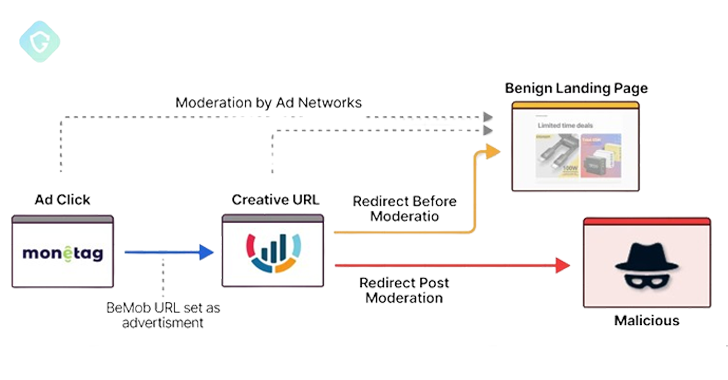
Guardio Labs mentioned it was capable of hint the origins of the marketing campaign to Monetag, a platform that claims to supply a number of advert codecs to “monetize web sites, social site visitors, Telegram Mini Apps,” with risk actors additionally leveraging providers like BeMob ad-tracking to cloak their malicious intent. Monetag can also be tracked by Infoblox below the names Vane Viper and Omnatuor.

The marketing campaign successfully boils all the way down to this: web site homeowners (i.e., risk actors) register with Monetag, after which site visitors is redirected to a Visitors Distribution System (TDS) operated by the malvertising advert community, finally taking guests to the CAPTCHA verification web page.
“By supplying a benign BeMob URL to Monetag’s advert administration system as a substitute of the direct faux captcha web page, the attackers leveraged BeMob’s popularity, complicating Monetag’s content material moderation efforts,” Tal defined. “This BeMob TDS lastly redirects to the malicious CAPTCHA web page, hosted on providers like Oracle Cloud, Scaleway, Bunny CDN, EXOScale, and even Cloudflare’s R2.”
Following accountable disclosure, Monetag has eliminated over 200 accounts linked to the risk actor. BeMob, in an identical effort, eliminated the accounts that had been used for cloaking. That mentioned, there are indicators that the marketing campaign has resumed once more as of December 5, 2024.
The findings as soon as once more spotlight the necessity for content material moderation and sturdy account validation to stop faux registrations.
“From misleading writer websites providing pirated or clickbait content material to complicated redirect chains and cloaking strategies, this marketing campaign underscores how advert networks, designed for reputable functions, may be weaponized for malicious actions,” Tal mentioned.
“The result’s a fragmented chain of tasks, with advert networks, publishers, advert statistics providers, and internet hosting suppliers every taking part in a task but typically avoiding accountability.”