In yet one more signal that menace actors are at all times searching for brand spanking new methods to trick customers into downloading malware, it has come to gentle that the question-and-answer (Q&A) platform often called Stack Trade has been abused to direct unsuspecting builders to bogus Python packages able to draining their cryptocurrency wallets.
“Upon set up, this code would execute mechanically, setting in movement a series of occasions designed to compromise and management the sufferer’s methods, whereas additionally exfiltrating their information and draining their crypto wallets,” Checkmarx researchers Yehuda Gelb and Tzachi Zornstain stated in a report shared with The Hacker Information.
The marketing campaign, which started on June 25, 2024, particularly singled out cryptocurrency customers concerned with Raydium and Solana. The checklist of rogue packages uncovered as a part of the exercise is listed beneath –
The packages have been collectively downloaded 2,082 occasions. They’re not out there for obtain from the Python Bundle Index (PyPI) repository.
The malware hid inside the package deal served a full-fledged data stealer, casting a large internet of knowledge, together with internet browser passwords, cookies, and bank card particulars, cryptocurrency wallets, and knowledge related to messaging apps like Telegram, Sign, and Session.
It additionally packed in capabilities to seize screenshots of the system, and seek for information containing GitHub restoration codes and BitLocker keys. The gathered data was then compressed and exfiltrated to 2 completely different Telegram bots maintained by the menace actor.
Individually, a backdoor element current within the malware granted the attacker persistent distant entry to victims’ machines, enabling potential future exploits and long-term compromise.
The assault chain spans a number of phases, with the “raydium” package deal itemizing “spl-types” as a dependency in an try to hide the malicious habits and provides customers the impression that it was professional.
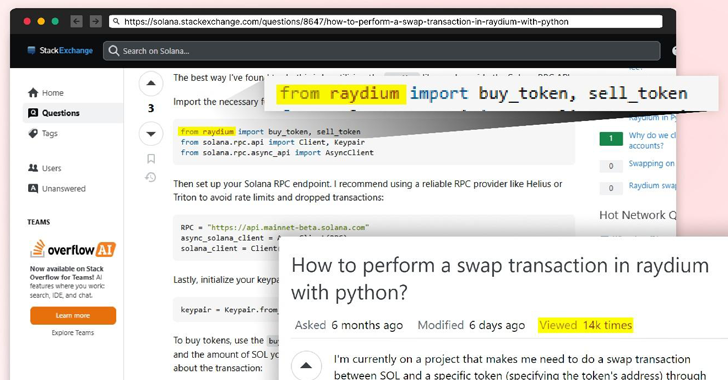
A notable facet of the marketing campaign is using Stack Trade as a vector to drive adoption by posting ostensibly useful solutions referencing the package deal in query to developer questions associated to performing swap transactions in Raydium utilizing Python.

“By selecting a thread with excessive visibility — garnering hundreds of views—the attacker maximized their potential attain,” the researchers stated, including it was finished so to “lend credibility to this package deal and guarantee its widespread adoption.”
Whereas the reply not exists on Stack Trade, The Hacker Information discovered references to “raydium” in one other unanswered query posted on the Q&A web site dated July 9, 2024: “I’ve been struggling for nights to get a swap on solana community operating in python 3.10.2 put in solana, solders and Raydium however I can not get it to work,” a person stated.
References to “raydium-sdk” have additionally surfaced in a put up titled ” Purchase and Promote Tokens on Raydium utilizing Python: A Step-by-Step Solana Information” that was shared by a person named SolanaScribe on the social publishing platform Medium on June 29, 2024.
It is at present not clear when the packages had been faraway from PyPI, as two different customers have responded to the Medium put up looking for assist from the writer about putting in “raydium-sdk” as just lately as six days in the past. Checkmarx advised The Hacker Information that the put up is just not the work of the menace actor.
This isn’t the primary time dangerous actors have resorted to such a malware distribution methodology. Earlier this Could, Sonatype revealed how a package deal named pytoileur was promoted through one other Q&A service referred to as Stack Overflow to facilitate cryptocurrency theft.
If something, the event is proof that attackers are leveraging belief in these community-driven platforms to push malware, resulting in large-scale provide chain assaults.
“A single compromised developer can inadvertently introduce vulnerabilities into a complete firm’s software program ecosystem, doubtlessly affecting the entire company community,” the researchers stated. “This assault serves as a wake-up name for each people and organizations to reassess their safety methods.”
The event comes as Fortinet FortiGuard Labs detailed a malicious PyPI package deal referred to as zlibxjson that packed options to steal delicate data, resembling Discord tokens, cookies saved in Google Chrome, Mozilla Firefox, Courageous, and Opera, and saved passwords from the browsers. The library attracted a complete of 602 downloads earlier than it was pulled from PyPI.
“These actions can result in unauthorized entry to person accounts and the exfiltration of private information, clearly classifying the software program as malicious,” safety researcher Jenna Wang stated.