With Gartner lately declaring that SOAR (safety orchestration, automation, and response) is being phased out in favor of generative AI-based options, this text will discover intimately 4 key safety automation use instances.
1. Enriching Indicators of Compromise (IoCs)
Indicators of compromise (IoCs), equivalent to suspicious IP addresses, domains, and file hashes, are important in figuring out and responding to safety incidents.
Manually gathering details about these IoCs from varied sources will be labor-intensive and decelerate the response course of.
Automating the enrichment of IoCs can tremendously improve the effectivity of your safety operations.
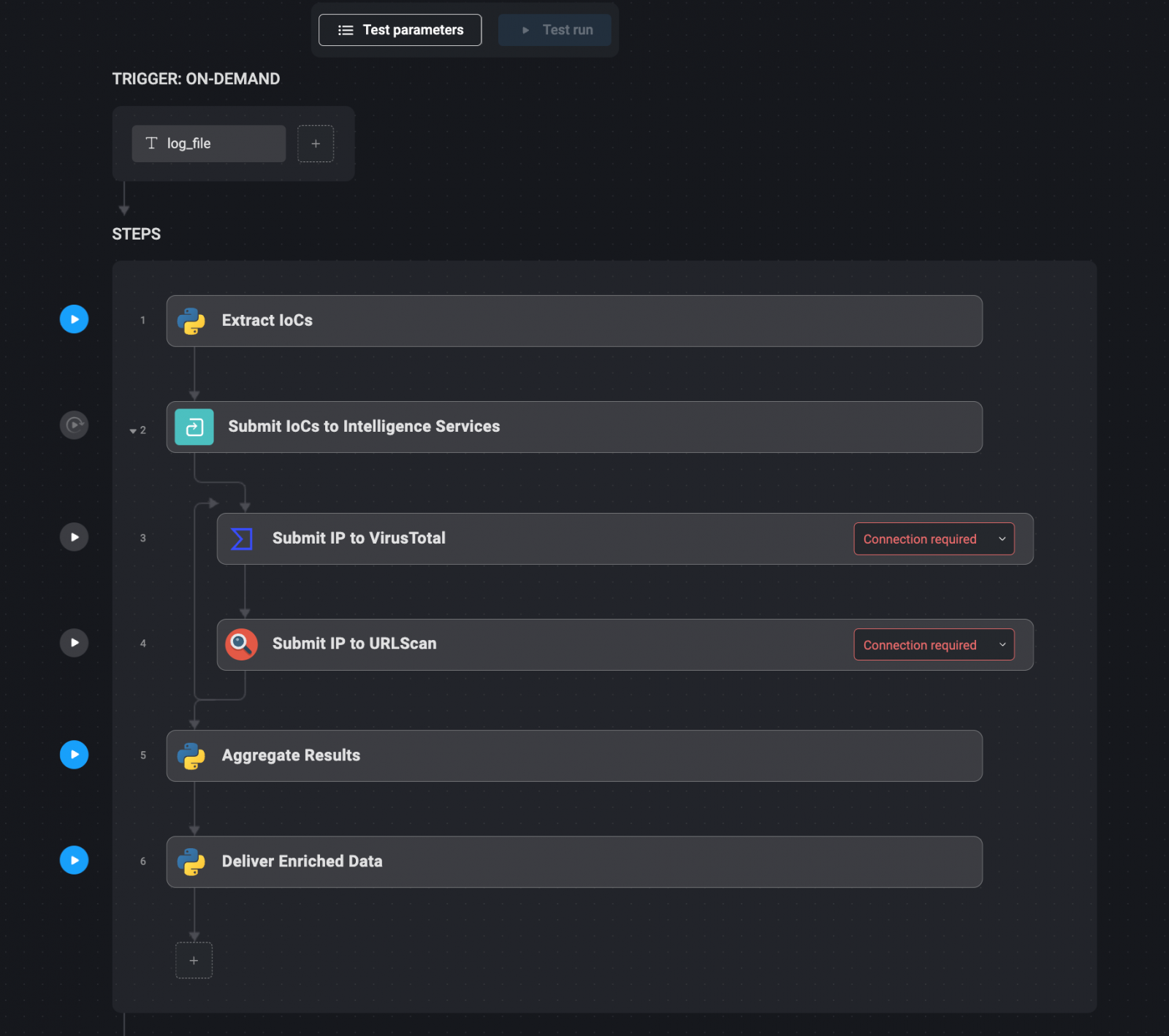
Automation workflow:
- Extract IoCs: Robotically extract related IoCs from safety logs or alerts utilizing textual content parsing instruments or different automated strategies.
- Submit IoCs to Intelligence Companies: As soon as extracted, the IoCs are mechanically submitted to varied risk intelligence companies, equivalent to VirusTotal, URLScan, and AlienVault, by way of their APIs. These companies can present further context, equivalent to whether or not the IP tackle has been related to identified threats or if the area has been flagged for suspicious exercise.
- Mixture Outcomes: The outcomes from these intelligence companies are aggregated right into a single, complete report. This step ensures that every one related data is on the market in a single place, making it simpler for safety analysts to evaluate the risk.
- Ship Enriched Information: The enriched IoC knowledge is then delivered by way of communication channels like Slack, or instantly added to the related incident ticket inside the safety administration system. This ensures that every one needed data is instantly accessible to those that want it.
2. Monitoring Your Exterior Assault Floor
The exterior assault floor of a company consists of all of the external-facing property that would probably be exploited by attackers.
These property embody domains, IP addresses, subdomains, uncovered companies, and extra.
Common monitoring of those property is vital for figuring out and mitigating potential vulnerabilities earlier than they’re exploited.
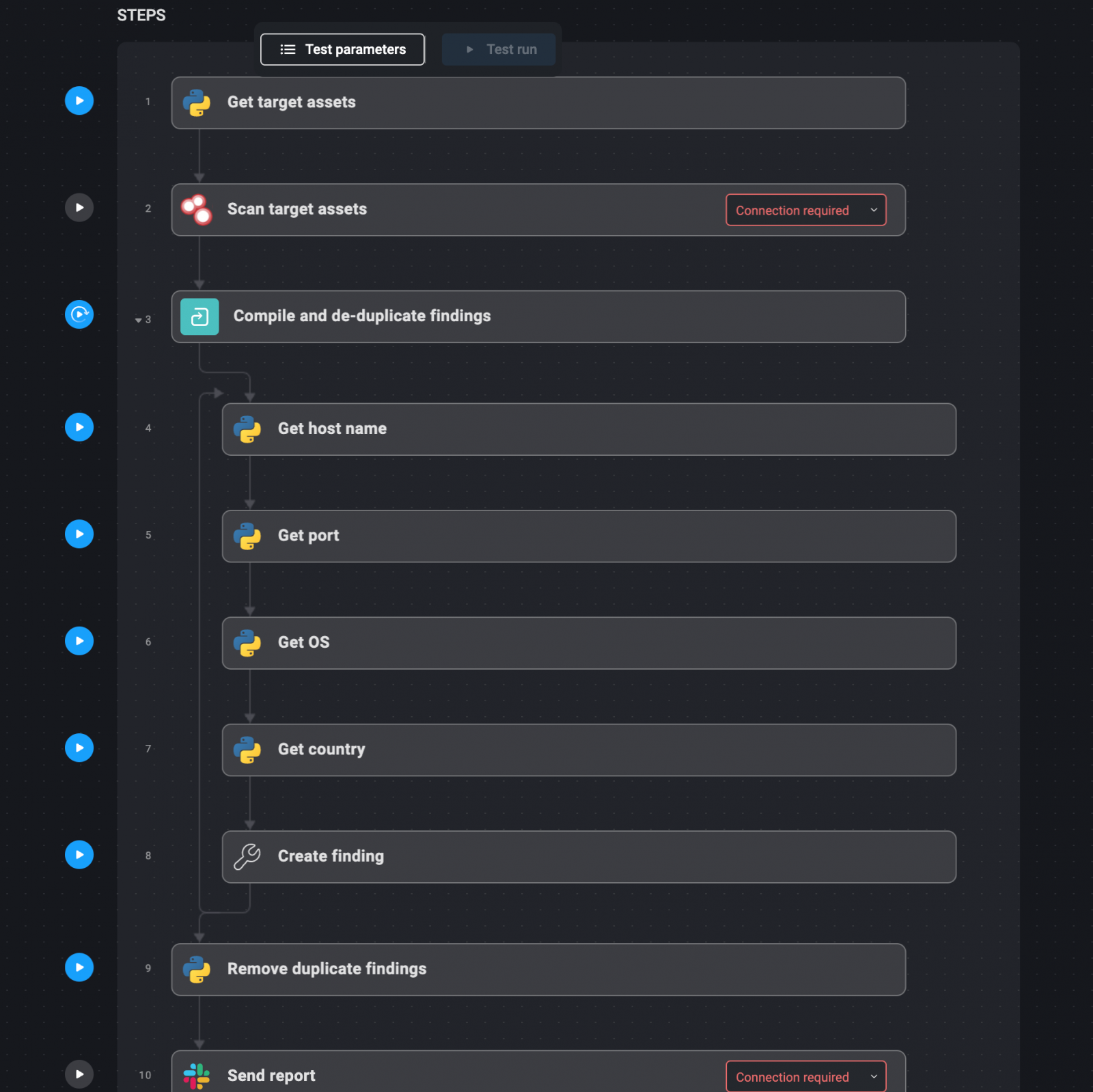
Automation workflow:
- Outline Goal Property: Begin by defining the domains and IP addresses that make up your exterior assault floor. These needs to be documented in a file that the automation system can reference.
- Automated Reconnaissance: Use instruments like Shodan to scan these property on a weekly or month-to-month foundation. Shodan might help establish open ports, uncovered companies, and different vulnerabilities.
- Compile and De-duplicate Findings: The outcomes from these scans are mechanically compiled right into a report. Any duplicate findings are eliminated to make sure that the report is concise and actionable.
- Ship Weekly Stories: The ultimate report is delivered by way of e mail, Slack, or one other most well-liked communication channel. This report highlights new or modified property, potential vulnerabilities, and any redundant functions that will pose a threat.
3. Scanning for Net Utility Vulnerabilities
Net functions are frequent targets for attackers, making common vulnerability scans helpful for sustaining safety.
Instruments like OWASP ZAP and Burp Suite automate the method of figuring out widespread vulnerabilities, together with outdated software program and misconfigurations.
These scans additionally detect enter validation vulnerabilities, serving to to safe net functions.
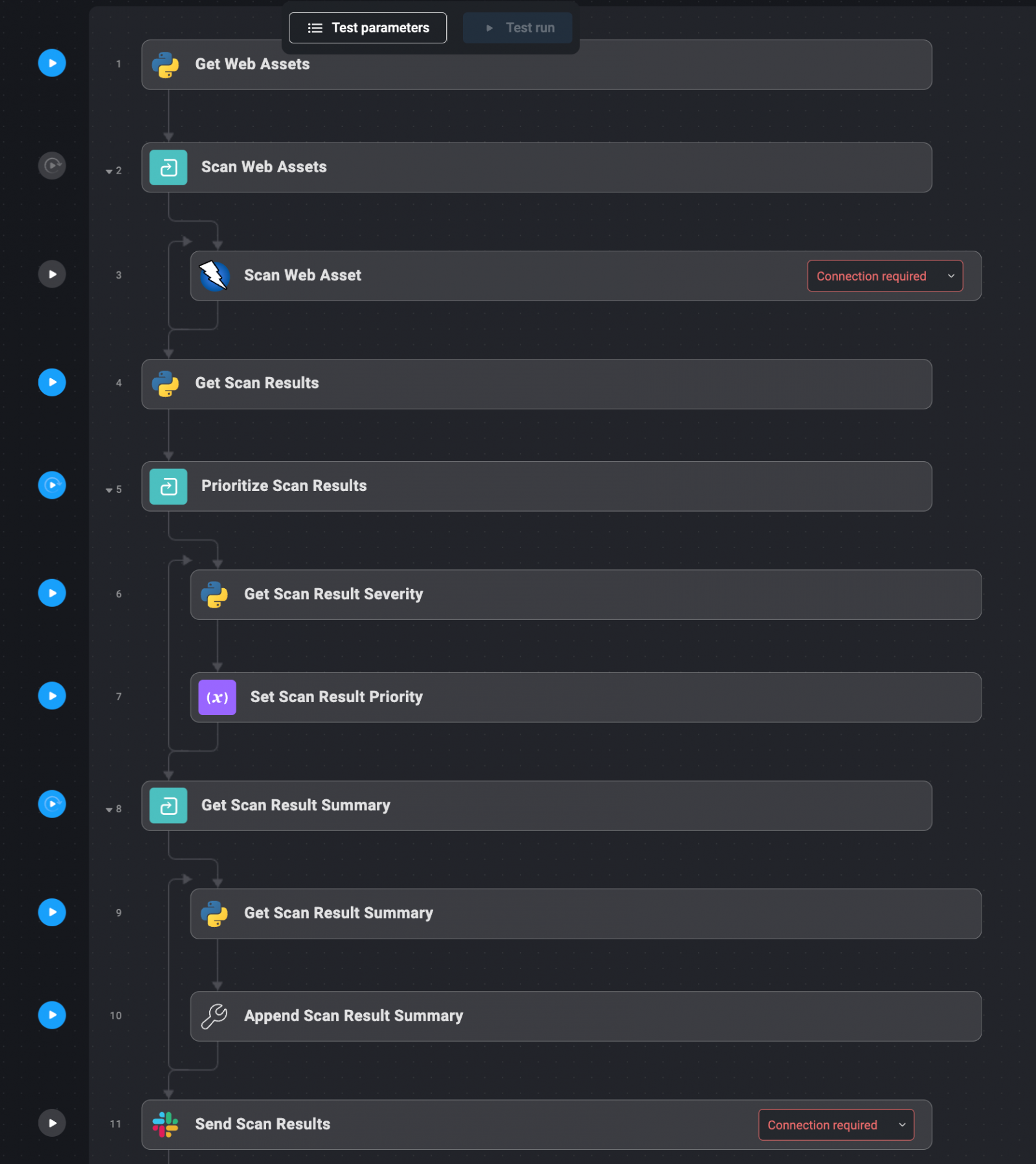
Automation workflow:
- Outline Net Property: Start by itemizing all of the domains and IP addresses that host your group’s net functions. These property needs to be documented in a file for straightforward reference by the automation system.
- Automated Vulnerability Scanning: The outlined net property are mechanically despatched to scanning instruments like OWASP ZAP and Burp Suite. These instruments carry out complete scans to establish vulnerabilities, together with these which can be generally exploited by attackers.
- Gather and Prioritize Outcomes: The outcomes from the scans are mechanically collected and prioritized based mostly on the severity of the vulnerabilities detected. Important/extreme vulnerabilities are highlighted for rapid motion.
- Ship Outcomes: The prioritized outcomes are delivered to the related groups by way of Slack or as an enriched ticket inside the incident administration system. This ensures that the appropriate individuals are notified of the vulnerabilities and may take acceptable motion.
4. Monitoring E-mail Addresses For Stolen Credentials
Monitoring for compromised credentials is a crucial side of a company’s cybersecurity technique.
Have I Been Pwned (HIBP) is a broadly used service that aggregates knowledge from varied breaches to assist people and organizations decide if their credentials have been compromised.
Automating the method of checking HIBP for uncovered credentials might help organizations rapidly establish and reply to potential safety incidents.
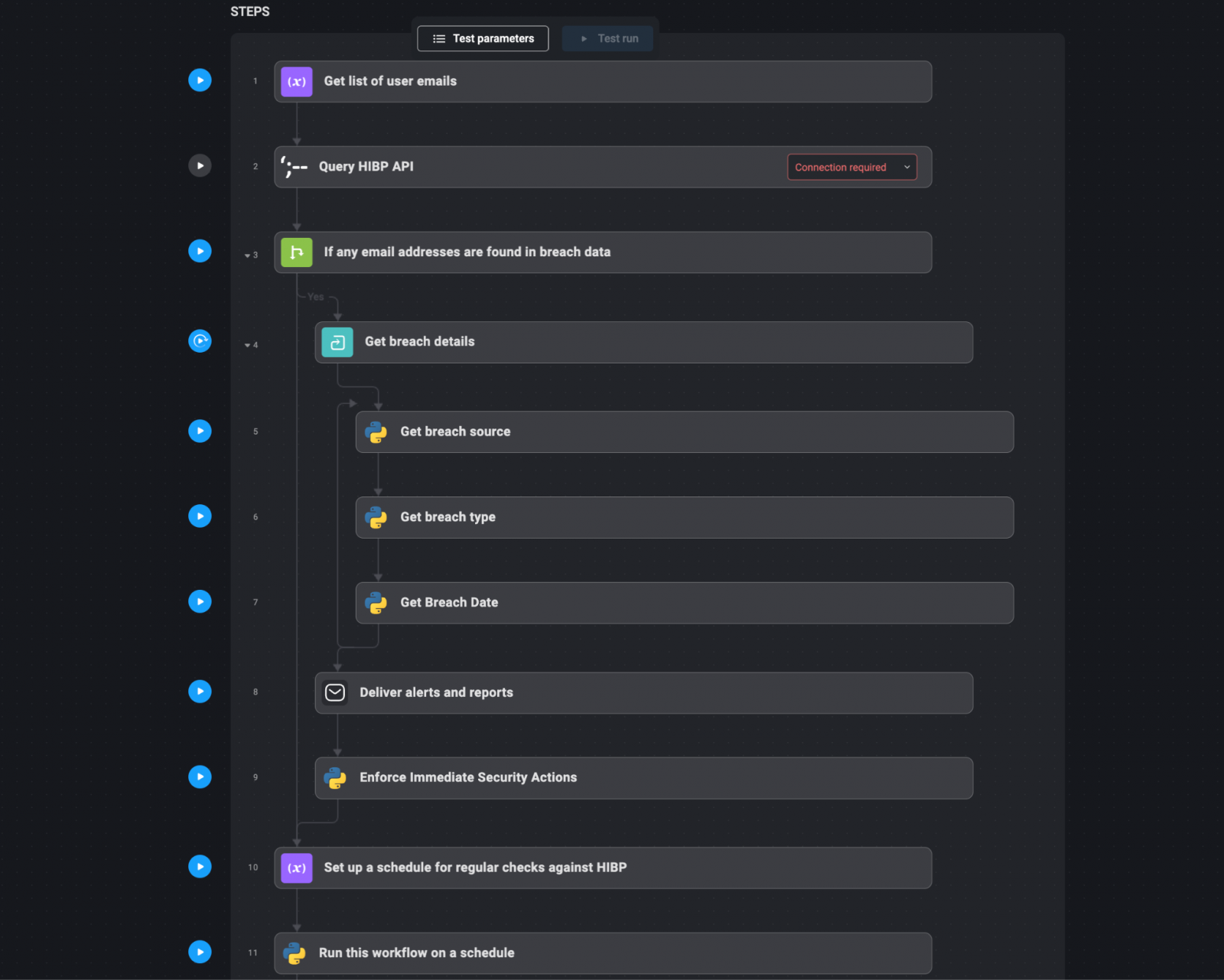
Automation workflow:
- Compile Person Emails and Domains: Create an inventory of person e mail addresses or domains that should be monitored. This listing ought to embody all related person accounts inside the group, particularly these with privileged entry.
- Question HIBP API: Robotically question the HIBP API with the compiled listing of e mail addresses or domains. This step entails sending requests to HIBP to test if any of the e-mail addresses have appeared in identified knowledge breaches.
- Mixture and Analyze Outcomes: Gather the responses from HIBP. If any e mail addresses or domains are present in breach knowledge, the main points of those breaches (such because the breach supply, sort of uncovered knowledge, and date of the breach) are aggregated and analyzed.
- Ship Alerts and Stories: If compromised credentials are detected, mechanically generate an alert. This alert will be despatched by way of e mail, Slack, or built-in into the group’s incident response system as a high-priority ticket. Embrace detailed details about the breach, such because the affected e mail addresses, the character of the publicity, and really helpful actions (e.g., forcing password resets).
- Implement Instant Safety Actions: Primarily based on the severity of the breach, the system can mechanically implement safety actions. For instance, it’d set off a password reset for affected accounts, notify the customers concerned, and enhance monitoring on accounts that had been compromised.
- Common Scheduled Checks: Arrange a schedule for normal checks in opposition to HIBP, equivalent to weekly or month-to-month queries. This ensures that the group stays conscious of any new breaches which may contain their credentials and may reply promptly.
Steadily Requested Questions
Under we’ll reply some ceaselessly requested questions concerning the automated workflows above and the way they might help in a sensible manner.
- Don’t third-party companies supply automation workflows anyway?
Many companies present APIs that permit for automating elements of the workflow, like fetching knowledge. Nevertheless, constructing an end-to-end automated workflow sometimes requires coding and configurations. Replicating your entire workflow with scripts gives flexibility however is much less highly effective, as modifications might break it. Leveraging accessible APIs with a centralized automation platform supplies a steady, scalable answer. - Can’t we simply replicate this complete factor with bash scripts?
Sure, it’s doable to write down Bash/PowerShell scripts to automate the safety duties talked about within the article. Scripts supply flexibility that’s missing in guide processes. Nevertheless, scripts require ongoing upkeep, and any modifications might break the workflow. They might additionally lack superior options like central administration, scheduling, alerting, and reporting, that are supplied by devoted automation platforms like Blink Ops. A correct platform is extra dependable and environment friendly for complicated, long-running automation necessities. - How does automating IoC enrichment assist?
Automating IoC enrichment hastens the response course of by gathering risk intelligence on indicators like IPs, domains, and file hashes from a number of sources concurrently by way of APIs. This supplies safety groups with a single complete report with the mandatory context to evaluate threats rapidly, relatively than spending time manually looking out completely different sources. It improves effectivity and situational consciousness, enabling knowledgeable choices to be made rapidly.
Enhance Your Cybersecurity Posture With Blink Ops
Blink is an ROI drive multiplier for safety groups and enterprise leaders who need to rapidly and simply safe a variety of use instances, together with SOC and incident response, vulnerability administration, cloud safety, identification and entry administration, and governance, threat, and compliance.
With 1000’s of automations within the Blink library and the power to customise workflows to suit your particular use case, Blink Ops can considerably enhance your safety operations.
Get began with Blink Ops.
Sponsored and written by Blink Ops.









