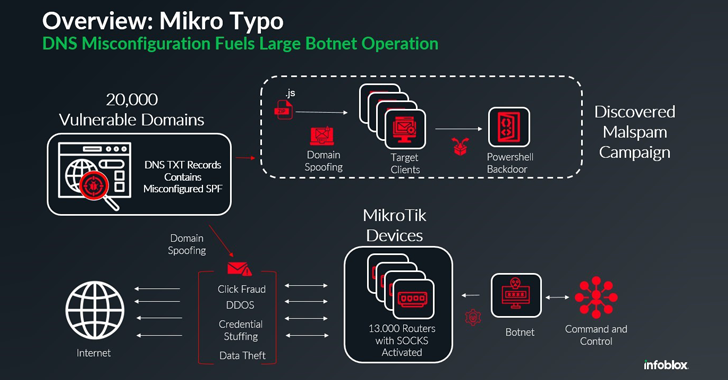
A world community of about 13,000 hijacked Mikrotik routers has been employed as a botnet to propagate malware by way of spam campaigns, the newest addition to a listing of botnets powered by MikroTik gadgets.
The exercise “take[s] benefit of misconfigured DNS information to cross electronic mail safety strategies,” Infoblox safety researcher David Brunsdon mentioned in a technical report revealed final week. “This botnet makes use of a world community of Mikrotik routers to ship malicious emails which might be designed to seem to return from legit domains.”
The DNS safety firm, which has codenamed the marketing campaign Mikro Typo, mentioned its evaluation sprang forth from the invention of a malspam marketing campaign in late November 2024 that leveraged freight invoice-related lures to entice recipients into launching a ZIP archive payload.
The ZIP file incorporates an obfuscated JavaScript file, which is then chargeable for operating a PowerShell script designed to provoke an outbound connection to a command-and-control (C2) server positioned on the IP tackle 62.133.60[.]137.
The precise preliminary entry vector used to infiltrate the routers is unknown, however numerous firmware variations have been affected, together with these susceptible to CVE-2023-30799, a crucial privilege escalation problem that may very well be abused to attain arbitrary code execution.
“No matter how they have been compromised, it appears as if the actor has been putting a script onto the [Mikrotik] gadgets that permits SOCKS (Safe Sockets), which permit the gadgets to function as TCP redirectors,” Brunsdon mentioned.
“Enabling SOCKS successfully turns every system right into a proxy, masking the true origin of malicious site visitors and making it tougher to hint again to the supply.”
Elevating the priority is the shortage of authentication required to make use of these proxies, thereby permitting different risk actors to weaponize particular gadgets or your entire botnet for malicious functions, starting from distributed denial-of-service (DDoS) assaults to phishing campaigns.
The malspam marketing campaign in query has been discovered to use a misconfiguration within the sender coverage framework (SPF) TXT information of 20,000 domains, giving the attackers the flexibility to ship emails on behalf of these domains and bypass numerous electronic mail safety protections.
Particularly, it has emerged that the SPF information are configured with the extraordinarily permissive “+all” choice, primarily defeating the aim of getting the safeguard within the first place. This additionally signifies that any system, such because the compromised MikroTik routers, can spoof the legit area in electronic mail.
MikroTik system house owners are really useful to maintain their routers up-to-date and alter default account credentials to stop any exploitation makes an attempt.
“With so many compromised MikroTik gadgets, the botnet is able to launching a variety of malicious actions, from DDoS assaults to knowledge theft and phishing campaigns,” Brunsdon mentioned. “The usage of SOCKS4 proxies additional complicates detection and mitigation efforts, highlighting the necessity for strong safety measures.”